Introduction to LAN Switches
To fasten the communication in different types of networks, Switches are the main fundamental part of networking. Switches can be connected from one network to another using node. These nodes help for efficient and speed communication. Switch exits in different types, and the basic functionality of a switch to provide the individual connection for every single node in an organization’s private network is meant as LAN switches.
LAN switches allow communication for particular network series that are connected as paired devices at that moment. And also, it allows to directly communicate with multiple users each other. The creation of switching provides free collision, high-speed in networking and makes the system parallel, quick and peer to peer connection is available between two devices.
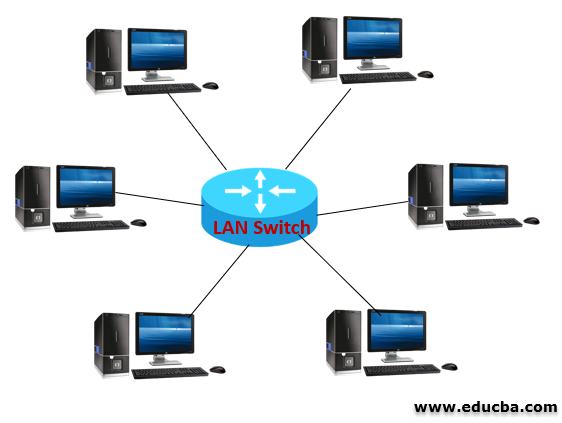
Working of LAN Switch
To have optimal network access in the devices, design alone is not sufficient for equipping. We should also concentrate on development. When the LAN network is designed, we need to remember a few things with a model’s development. They should be,
- Ease in switch managements and its configurations
- Use of VLAN – segmentation in network & traffic management in broadcasting
- Minimal Redundancy
- Secured network
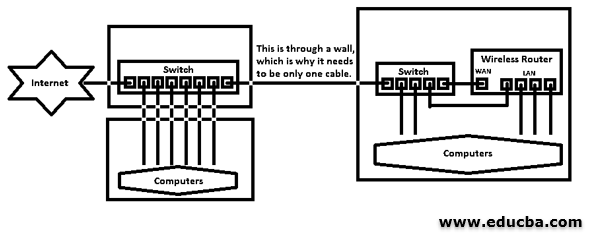
In order to learn how LAN switches work, we need to know the Hierarchical Model in LAN architecture. The hierarchical model comprises the following layers:
1. Access Layer Switch
The access layer is the lowest layer that connects to various devices, like computers, printers, IoT devices, etc. Switching at the access layer level would allow prioritizing network packages and bandwidth management between devices according to their priority.
2. Distribution Layer Switch
Distribution layer in between access and core layers. Distribution layer switches might be less significant compared to other switches, but they still play an important role in aggregating data and faster switching between the access layers. Popular Course in this categoryAll in One Software Development Bundle (600+ Courses, 50+ projects)600+ Online Courses | 3000+ Hours | Verifiable Certificates | Lifetime Access
4.6 (3,144 ratings)Course Price
₹8999 ₹125000
View Course
Related CoursesWindows 10 Training (4 Courses, 4+ Projects)JWS Java Web Services Training (4 Courses, 11 Projects)Java Training (40 Courses, 29 Projects, 4 Quizzes)
3. Core Layer Switch
The core layer is the topmost layer in the hierarchical model and consists of the fastest switches that connect the external networks to the lower layers of the model, catering to the highest bandwidth requirements of the devices in the network.
LAN Switch Setup
Switches in every layer are programmed to prioritize based on various factors as below:
1. Hostnames
Hostnames, console lines, VTY lines are basic configurations in switches for configuration to prioritize the devices and respective layers. Network administrators program switches with these parameters for immediate / Adhoc configurations.
2. Duplex
Duplex settings in switches can be categorized as Full duplex and half-duplex modes, which corresponds to the single and dual-way exchange of network packets at the moment. The duplex settings were once a crucial part of switch configuration, so network administrators had to configure them manually based on other network parameters. However, modern LAN switches come in the full-duplex configuration by default, along with the respective configuration. This helps to ease out administrators with just high-level duplex settings.
3. Port Security
Port security is an important thing, as they prevent from breaching. There are many breaches in security that switches can be attacked or harmed. Such attacks are MAC address flooding, spoofing, etc. MAC address flooding – This attack is performed by sending an invalid source address to the switch. They perform this by gaining access to a switch through nodes. The switch usually operates by adding the MAC address to its address table. It has a certain limit number for adding the address. During this attack, the database can be filled, and the switch fails to forward the traffic through unicast, and it begins to behave like the hub and start to flood the frames due to fewer ports. With the attack, the attacker can is eased to view all the frames of the network nodes.
4. Mac Address Spoofing
The attacker exposes itself as a DCHP server. When the clients try requesting the addresses from the server, the address is responded back, where it gets permitted to view all the traffic from a specific node itself. So the attacker can easily hit the client’s information through a server attack.
Other attacks can be performed by manipulating the switch with the ease of fragile technology or telnet. When the switch ports or the port interfaces are secured before the switch deployment, this security will limit the mac address numbers and validates which are allowed on the port.
Mac address is the addresses of the network containing 48 bits represented in hexadecimal numbers. In the layer 3 address, 2 parts for IP address & mac address is segregated into 2 parts: An identifier – uniquely identifies the organization (24 bits) & Number assigned to Vendor (24 bits). Usually, the complete address is hardcoded on the hardware of the switch & it cannot be changed once hardcoded.
Benefits of LAN switch
- Increased scalability – As the business’s bandwidth increases, the network can be expanded by its own growth.
- Performance of bandwidth – The bandwidth performance is improved for all individual users in the network environment. Users may be using applications like multimedia, or they can have frequent interaction with client-server databases. There won’t be any lag during their interactions.
- Zero network failure – With a properly designed network, the network failure has very few chances; the user will experience seamless network connectivity.
- Less congestion & delay in transmission of the message – The segmentation of the network helps to minimize the difficulty in a user’s access to the network. This is reduced as the bandwidth of LAN on availed on each segment. Access becomes more efficient in business applications.
- Parallel connectivity – When the devices are paired and connected through switch ports, we can transfer various data at the same time simultaneously. This feature is not possible when connected through hub-based networks.
- Tractable and secured through VLANs – VLANs helps to stay connected with network transfer; though there are physical changes in the environment, it keeps functionally intact with no reconfiguration. This helps individual users easily manage and secure connection in workgroups and perform business functions based on common interests. This gives flexibility for users to move around and have the same connectivity with other users.
Conclusion
The LAN switch can be configured in many ways using commands too. Here we have gone through the basic operations and set up of the LAN switch. These help to verify and troubleshoot the problems over switching operations.
Recommended Articles
This is a guide to How does LAN Switches work?. Here we discuss LAN Switch Setup, the Working and Benefits of LAN switch. You may also look at the following articles to learn more-
